-
KEYRKE(키르케)
클라우드 네이티브 환경과 멀티클라우드 환경의 비밀자산관리 솔루션
-
CyberArk
권한 접근 관리(Privileged Access Management)의 글로벌 리더
-
Digital Guardian
업계 유일의 엔터프라이즈 DLP 용 SaaS 솔루션
-
Imperva
애플리케이션과 API를 보호하는 사이버 보안 리더
-
Skyhigh Security
클라우드 보안 중심의 Skyhigh Security
-
Trellix
동적 위협에 대응하는 데 필요한 적응형 보호 기능
-
MontaVista
Embedded Linux 상용화의 선두주자
-
Trend Micro
기업/데이터 센터/클라우드 환경/네트워크 및 엔드포인트 보안 솔루션
-
Check Point
글로벌 1위, 차세대 방화벽
-
Monitorapp
국내 웹방화벽 시장점유율 1위!, 시큐어 웹게이트웨이(SWG), SSL 가시성 솔루션 제공
-
eNsecure
애플리케이션 위변조 방지 및 API 이상징후 탐지 및 관리, 기업의 모바일 엔드포인트 및 모바일 애플리케이션 보안
-
McAfee
엔드포인트에서 클라우드까지 위협 인텔리전스 통합 솔루션
-
DONGHOON Itech
보안점검 비용 절감 및 상시보안점검 체계 구축을 위한 동훈아이텍 솔루션
Cloud Computing Security
동훈아이텍은 전세계에서 가장 먼저, 그리고 가장 많은 고객을 가지고 있는 모든 영역의 클라우드 보안 솔루션을 제공하고 있습니다.
Cloud Computing Security 란 무엇입니까?
- 모든 산업 분야에 클라우드가 확산되면서 클라우드 보안은 선택이 아닌 필수가 되었고 클라우드에서의 보안은 기존 On-Premise 환경에서의 경계 보안과는 완전히 다릅니다. 클라우드에서는 경계 그 자체가 없어지기 때문에 워크로드 자체에 대한 보안의 중요성이 커지고 워크로드 에 대한 접근 제어와 권한 관리의 중요성이 커지고 있습니다.
최근에는 클라우드에서의 배포 관리의 편의를 위한 어플리케이션 패키징 형태의 컨테이너 활용이 늘어나고 있으며 현재의 클라우드 보안은 컨테이너 보안까지의 확장을 의미하고 있습니다.
- 왜 Cloud Computing Security 가 필요합니까?
-
클라우드는 언제 어디서든 손쉽게 워크로드에 접근할 수 있으며 이로 인하여 워크로드 자체에 대한 보안 및 워크로드 접근제어 솔루션이 반드시 필요 합니다. 워크로드 자체에 대한 보안은 백신 기능뿐만 아니라 IDS/IPS, Firewall과 같은 On-Premise의 경계 보안을 담당했던 기능들도 필요 합니다. 또한 Application 자체를 보호할 수 있는 기능과 Log에 대한 무결성, 그리고 Zero-day Attack을 방어할 수 있는 Threat Intelligence를 이용한 실시간 위협 업데이트 기능을 가지고 있어야 합니다.
또한 다양한 SaaS로 제공되는 서비스를 이용할 때 SSO(Single Sign-On)와 멀티팩터인증(MFA)을 제공해야 하며 각각의 워크로드에 대한 취약점 점검, 상태 모니터링, 컴플라이언스 체크를 통한 형상 관리를 해야 합니다.
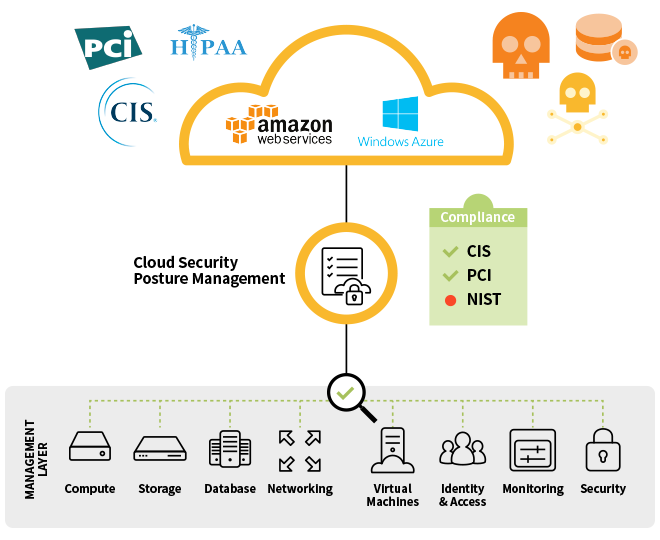
- 어떤 역량이 포함됩니까?
-
클라우드에서 보안 적용을 도입 검토하신다면 다음과 같은 내용을 고려해야 합니다.
1. 워크로드에서 권한 있는 자격증명에 대한 중앙 집중식 보안 및 접근제어가 가능해야 합니다.
- 권한이 있는 계정의 자격 증명(암호 및 SSH 키)에 대한 자동 로테이션으로 시간소요가 크고 오류가 자주 발생하는 불필요한 작업을 제거합니다.
- 이를 통해 클라우드 환경에서 자격 증명 및 기밀을 보호 할 수 있습니다.2. 워크로드에 Anti-Malware 와 컨텐츠 필터링이 가능해야 합니다.
- 진화하는 멀웨어(Malware)의 위협으로부터 윈도우와 리눅스의 워크로드를 보호하고 클라우드 보안센터에서 새로 생겨나는 위협에 대한 실시간 업데이트가 가능해야 합니다.3. 방화벽 및 호스트기반 침입탐지 및 방지가 가능해야 합니다.
- 양방향 호스트 기반 방화벽을 이용하여 컴플라이언스 보고를 위해 워크로드 레벨의 트래픽을 기록하고 감사(audit)할 수 있습니다.
- Shellshock과 같은 취약점 공격을 방지하고 네트워크 패킷 분석, 악성 또는 의심스러운 트래픽 차단을 통해 워크로드를 보호합니다. 의심스러운 행위에 대한 Timeline 기준의 상관관계 정보가 제공되는지 확인해야 합니다.4. 로그 감사 및 무결성 모니터링이 가능해야 합니다.
- 호스트기반 모니터링을 통해 파일, 포트, 레지스트리 등에 대해 승인되지 않거나 또는 정책에 어긋나는 변경사항을 감지하여 경고합니다.
- 다양한 환경의 로그를 분석, 정의하여 잠재적인 보안 이벤트에 대한 가시성을 제공합니다.
- 의심스러운 이벤트를 SIEM 시스템 또는 중앙 로깅 서버에 전송하여 상관관계를 파악, 보고 및 보관합니다. 그 외에 “경고 분류와 필터링”, “다중위협보호”, “다른 솔루션과의 연동” 등을 고려해야 합니다.5. 워크로드에 자동화된 보안 및 컴플라이언스 검사가 가능해야 합니다.
- 컴플라이언스 표준 (PCI, GDPR, HIPAA, NIST 등)과 클라우드 보안 모범 사례 규칙을 이용한 클라우드 인프라에 대한 보안 사항과 컴플라이언스 준수 상태 검사 가 가능합니다.
- 어떤 장점을 갖고 있습니까?
-
동훈아이텍에서 Cloud Computing Security 기능을 가진 다음과 같은 솔루션을 취급 합니다.
1. 온-프레미스, 하이브리드 및 클라우드 환경에서 권한 접근 관리 분야의 리더인 CyberArk의 Privileged Access Manager
2. SaaS Service에 대한 SSO와 MFA기능을 제공하는 CyberArk의 Workforce Identity
3. 클라우드 워크로드의 All-in-One 보안 솔루션인 TrendMicro의 클라우드워크로드보안(CWPP)솔루션
4. 클라우드 인프라에 대한 보안, 규정 준수 및 거버넌스 솔루션인 클라우드워크로드형상관리 솔루션(CSPM)인 Conformity
5. 클라우드에서의 웹어플리케이션 보안 및 DDoS방어를 제공하는 Imperva의 FlexProtect
위 클라우드 보안 솔루션의 장점은 모두 각 분야의 세계 1위 제품으로 가장 많은 클라우드 도입 고객사의 보안 적용에 대한 경험을 가지고 있다는 장점을 가지고 있습니다. 또한 동훈아이텍은 클라우드 보안에 필요한 모든 영역의 보안 솔루션을 보유하고 있습니다. 많은 고객들이 클라우드로 전환하고 있지만 클라우드에 대한 보안 적용은 이제 시작 단계 입니다. 아직 잘 모르는 영역에서의 경험은 가장 중요한 요소이며 동훈아이텍은 전세계에서 가장 먼저, 그리고 가장 많은 고객을 가지고 있는 모든 영역의 클라우드 보안 솔루션을 제공하고 있습니다.
- 고객에게 어떤 도움을 줍니까?
-
클라우드로의 전환을 앞둔 고객과 전환을 마무리한 고객들은 이제 과거의 On-Premise에 적용한 보안을 어떻게 적용해야 하는지에 대한 고민이 큽니다. 클라우드 자체는 경계라는 것이 존재하지 않기 때문에 기존의 방식과는 완전히 다르며 이는 어떻게 시작해야 하는지조차 혼란스러울 수 있습니다.
동훈아이텍의 클라우드 사업부에서는 20여년 동안의 보안 경험을 바탕으로 이러한 고민을 해결하고 모든 고객이 클라우드 환경에서 단 한 건의 보안 사고 없이 서비스를 제공할 수 있도록 도와 드리겠습니다.